JSON/XML Injection
JSON Injection
E.g. if the server uses code like
String username = JSON.parse(json).get("username");
String password = JSON.parse(json).get("password");
sendToUserService(
"{ \"account\": \"user\" \"username\": \"" + username + "\", \"password\": \"" + password + "\" }"
);
an attacker could modify the password parameter that the resulting JSON looks like
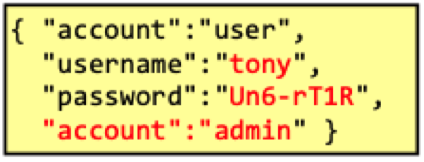
which is still valid JSON and depending on how the JSON parser on the user service behaves, it might create an admin account.
XML External Entity Injection
If the server uses an XML parser which has external entities enabled, sending something like
<?xml version="1.0" encoding="ISO-8859-7" ?>
<!DOCTYPE foo [ <!ENTITY attack SYSTEM "file:///etc/passwd"> ]>
<report>
<username>admin</username>
<content>&attack;</content>
</report>
would cause the parser to read the file /etc/passwd and insert it into content.
Countermeasures
- Input validation: Check all data provided by the user before inserting them into JSON / XML data structures
- Configure the XML parser to not resolve external entities
- Don't use XML but use less complex data formats such as JSON or YAML