Security Requirements Engineering and Threat Modeling
Threat modeling is closely associated with security requirements engineering. The purpose of threat modeling is to identify security design flaws.
The Security Requirements Engineering Process
- Identify the business and security goals of a system
- Express the business goal in one or few sentences
- Driven by the business goal, identify a few security goals
- Collect information about the system so you get a good understanding of its purpose and how it works
- This includes answering questions like
- What functions does the system provide?
- Who uses the system?
- What data does the system process?
- What are the most important assets of the system?
- How does the system work (components, technologies, interactions, ...)?
- What is the service level (24/7 or only workdays)?
- What security requirements or controls have already been defined?
- Determine the most valuable assets (Person user data, credentials, logs, ...)
- This includes answering questions like
- Decompose the system to understand its internal workings and as a basis for the following step
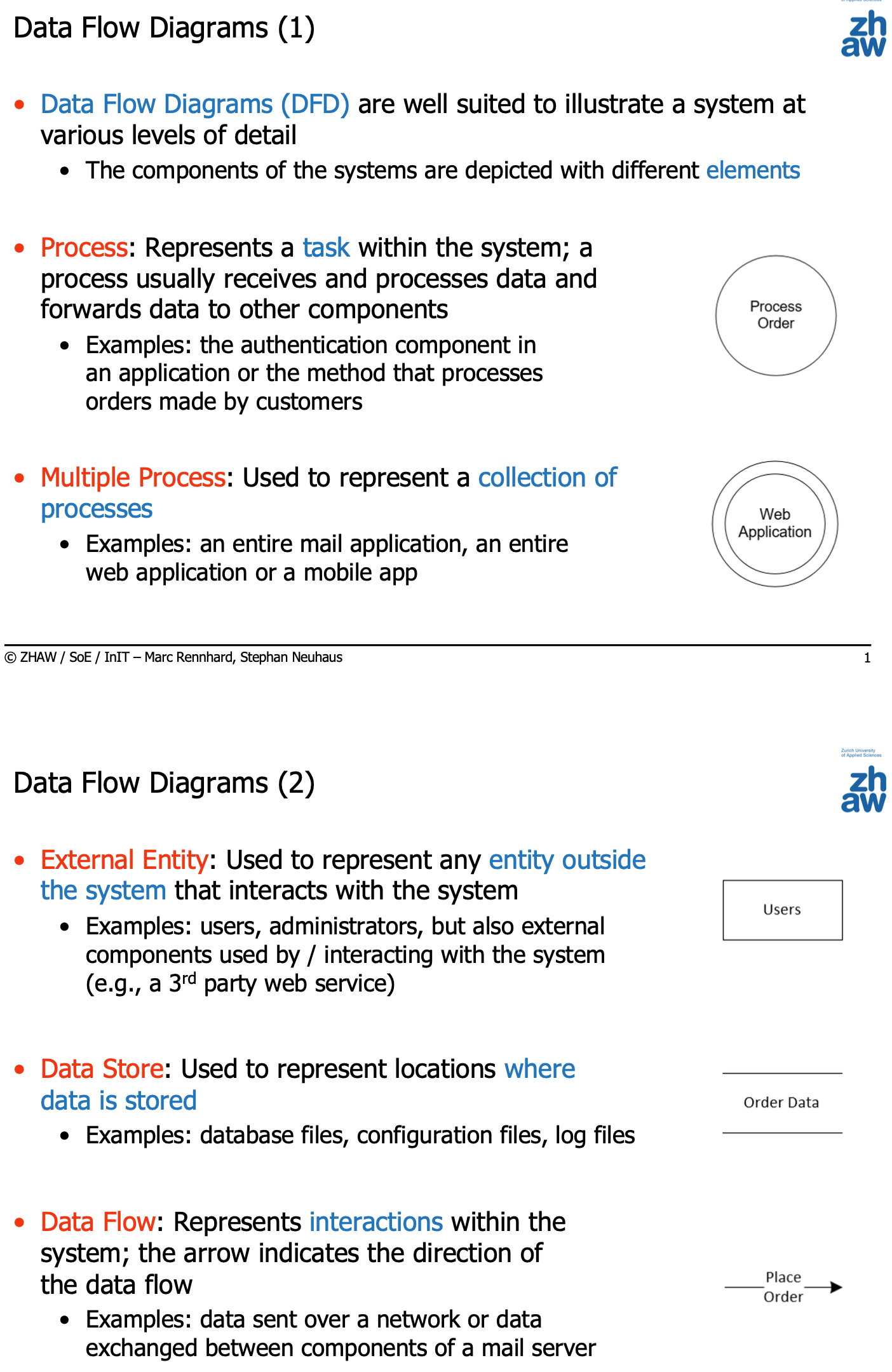
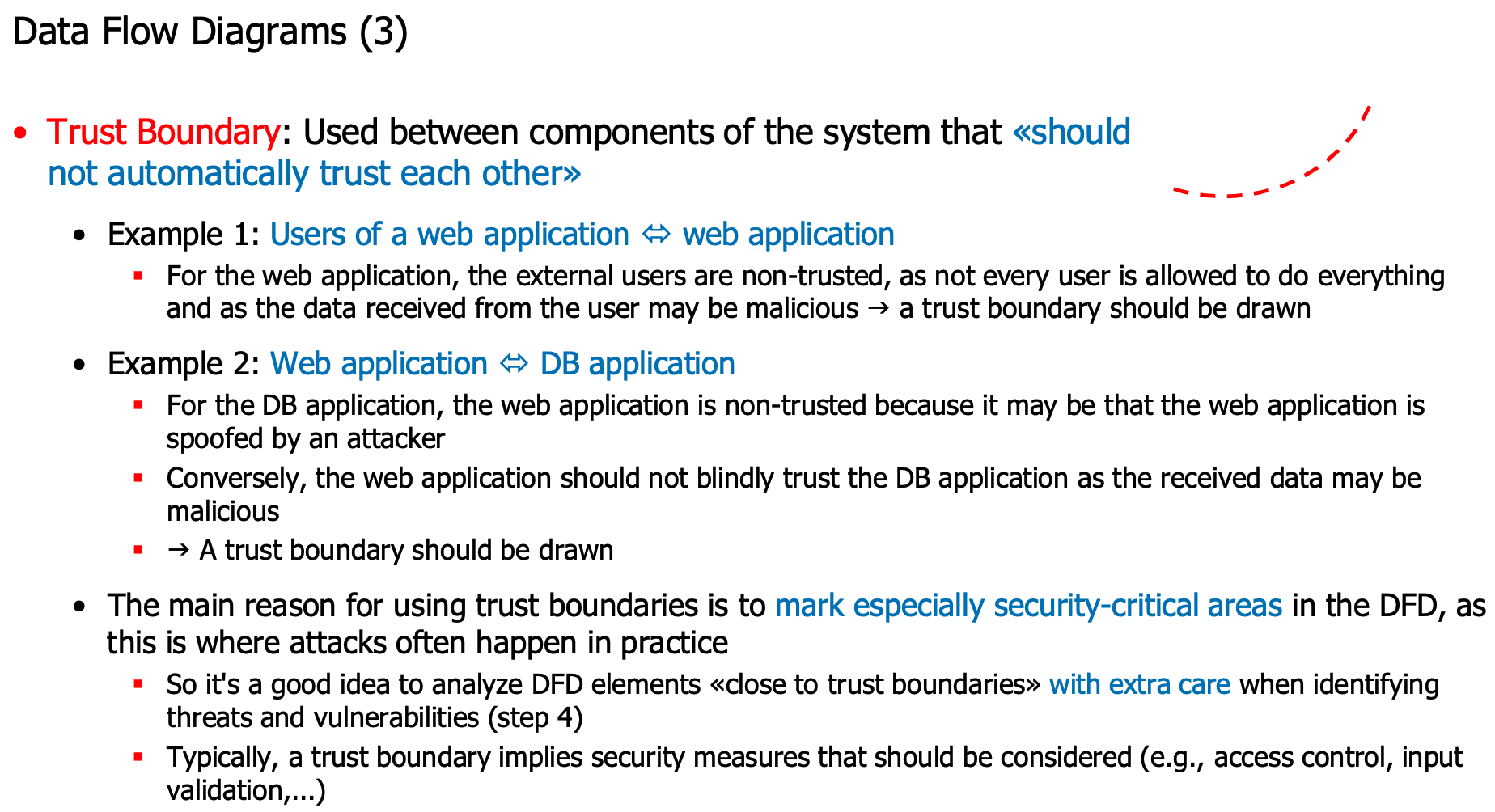
- Draw a network diagram, data flow diagram, etc.
- Identify threats that are relevant for the system and rate the risk of these threats
- Use the STRIDE method to identify threats:
- For each DFD element, identify possible threats / attack scenarios
- Focus on realistic threats given the assumed threat agent and their goals
- Rate the security risk by taking into account the existing security controls
- If the risk of a threat is too high, then a vulnerability has been identified
- Use the STRIDE method to identify threats:
- Mitigate the threats where necessary by proposing adequate security requirements that bring down the risks to
acceptable levels
- Define new security requirements
- Document threats and security requirements for all subsequent security activities
Data Flow Diagrams
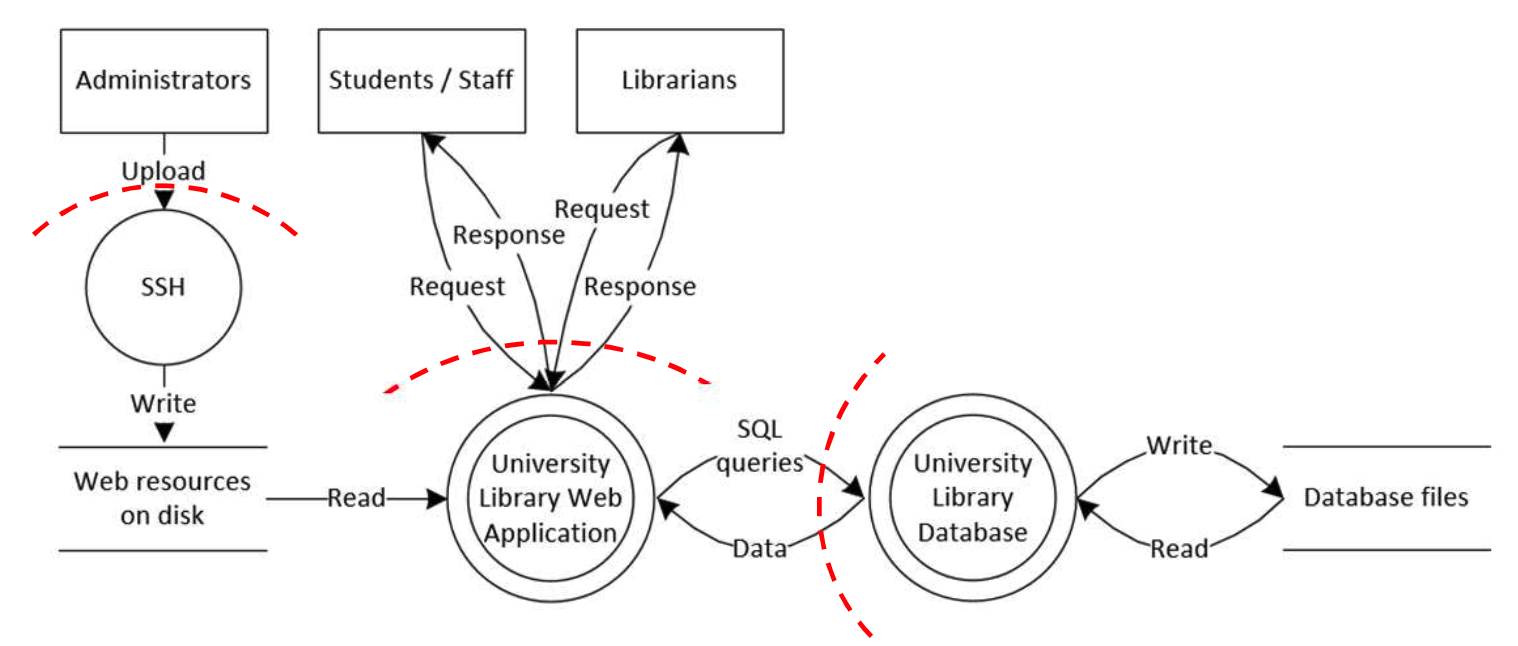
Example diagram:
STRIDE
- Spoofing
- Attacker pretends to be somebody or something else (e.g., another user or another server)
- Examples: Accessing a system with another user's identity, e-mail spoofing, e-banking server spoofing to collect credentials during a phishing attack,...
- Tampering
- Attacker modifies data or code in a malicious way (at rest or in transit)
- Examples: Modifying a file with insufficient access protection (e.g., world-writeable), modifying data sent across unprotected network links (e.g., replies from a DNS server),...
- Repudiation
- A repudiation threat exists if an attacker can deny having performed an action because there's no evidence to link the action to the attacker
- Examples: An e-banking admin who increases the balance of his own bank account and manipulates the log files to remove all traces,...
- Information disclosure
- Attacker gets access to information he's not authorized to read
- Examples: Reading files with plaintext passwords, reading credit card data sent across unprotected network links, reading data from the database using SQL injection,...
- Denial of service
- Attacker prevents legitimate users from accessing the system
- Examples: Crashing an application or a system (triggering an exception, causing a buffer overflow), flooding a system with large amounts of network traffic,...
- Elevation of privilege
- Attacker gets more privileges than he is entitled to
- Examples: Exploiting a vulnerable program that runs with administrator rights, circumventing a poor access control mechanism,...
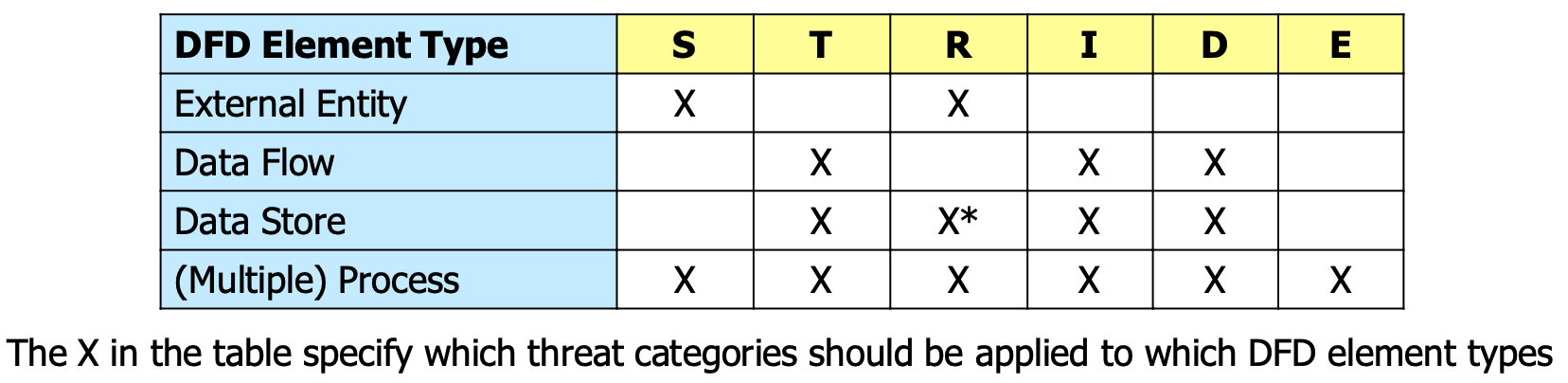
To identify the threats against a specific system, the STRIDE categories are applied to the DFD elements according to the following table:
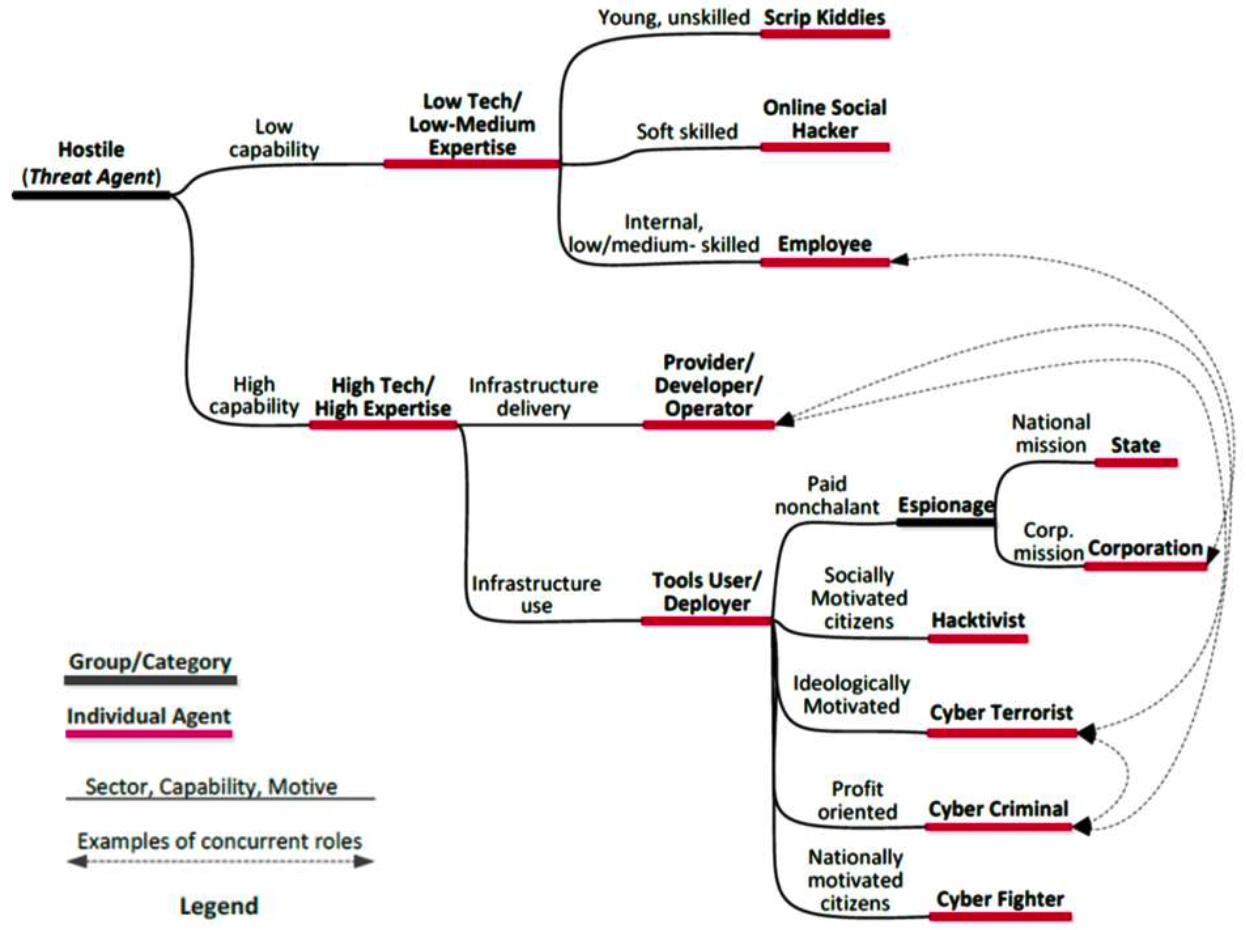
Before applying STRIDE to the DFD, the threat agents (according to ENISA) should be identified: