Secure the Weakest Link / Defense in Depth / Fail Securely / Principle of Least Privilege / Separation of Privileges / Secure by Default / Minimize Attack Surface / Keep Security Simple / Avoid Security by Obscurity / Don't Trust User Input and Services
Fundamental Security Principles
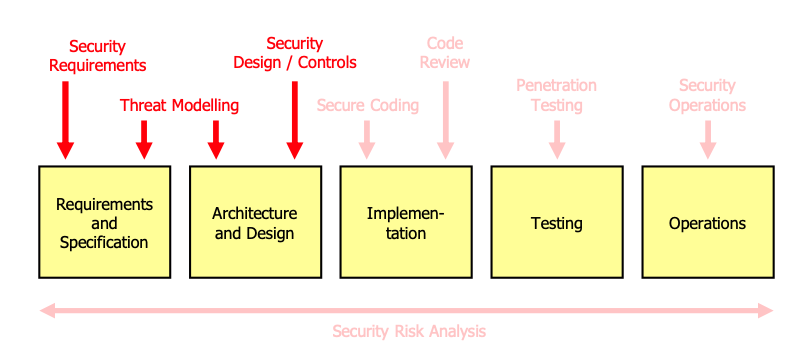
Covers the following security activities:
Secure the Weakest Link
The overall security of a system with different components is determined by the weakest component.
This basically means fixing the issues rated as high risk first.
Defense in Depth
Risks should be mitigated by multiple layers of security so that if one layer fails, the others will still protect the system.
Some examples:
- Also encrypt internal traffic even if a firewall is in place
- Harden not only exposed servers, but also internal servers
A powerful strategy should include mechanisms to prevent, detect, contain and recover from attacks. For example, for a web service using passwords:
- Prevent the use of weak passwords
- Detect brute force attacks by monitoring logs
- Contain the attack by blocking the attacker's IP address
- Recover from the attack by resetting the password and require users to change their passwords
Fail Securely
If a system fails, it must not compromise the security of the system. (e.g. if login failed, the user should not be able to access the system)
Another example is poor configuration of a system, if it for example allows to fail to an older version of the protocol, so that an attacker can downgrade the protocol and exploit a vulnerability.
Principle of Least Privilege
A user and a program should only have the permissions he needs to perform his job.
Separation of Privileges
By separating privileges, a single user cannot carry out or conceal an action completely on his own. For example, database administrators should not also be administrators of the operating system.
In practice it's often not possible to separate privileges completely, but it's important to separate them as much as possible.
Secure by Default
Programs should be implemented / delivered / installed with secure default configurations.
Minimize Attack Surface
The attack surface is the set of all possible attack vectors. The smaller the attack surface, the easier it is to secure the system.
Keep Security Simple
Make sure that security is designed and implemented in a way that is easy to understand and maintain, using proven software components and techniques. Also, implement security-critical features only once.
Help the user by explaining him what he needs to do to secure the system, don't provide insecure options and don't allow them to temporarily disable security features (like certificate warnings in browser).
Avoid Security by Obscurity
Relying on the secrecy of a system to protect it is generally not a good idea because of powerful reverse engineering methods. It may be used to make it harder but it is virtually impossible to prevent attacks by trying to hide something.
Don't Trust User Input and Services
In general, it should be assumed that user input and services are malicious. Therefore, always validate data before processing it.