Secure Development Lifecycle (SDL)
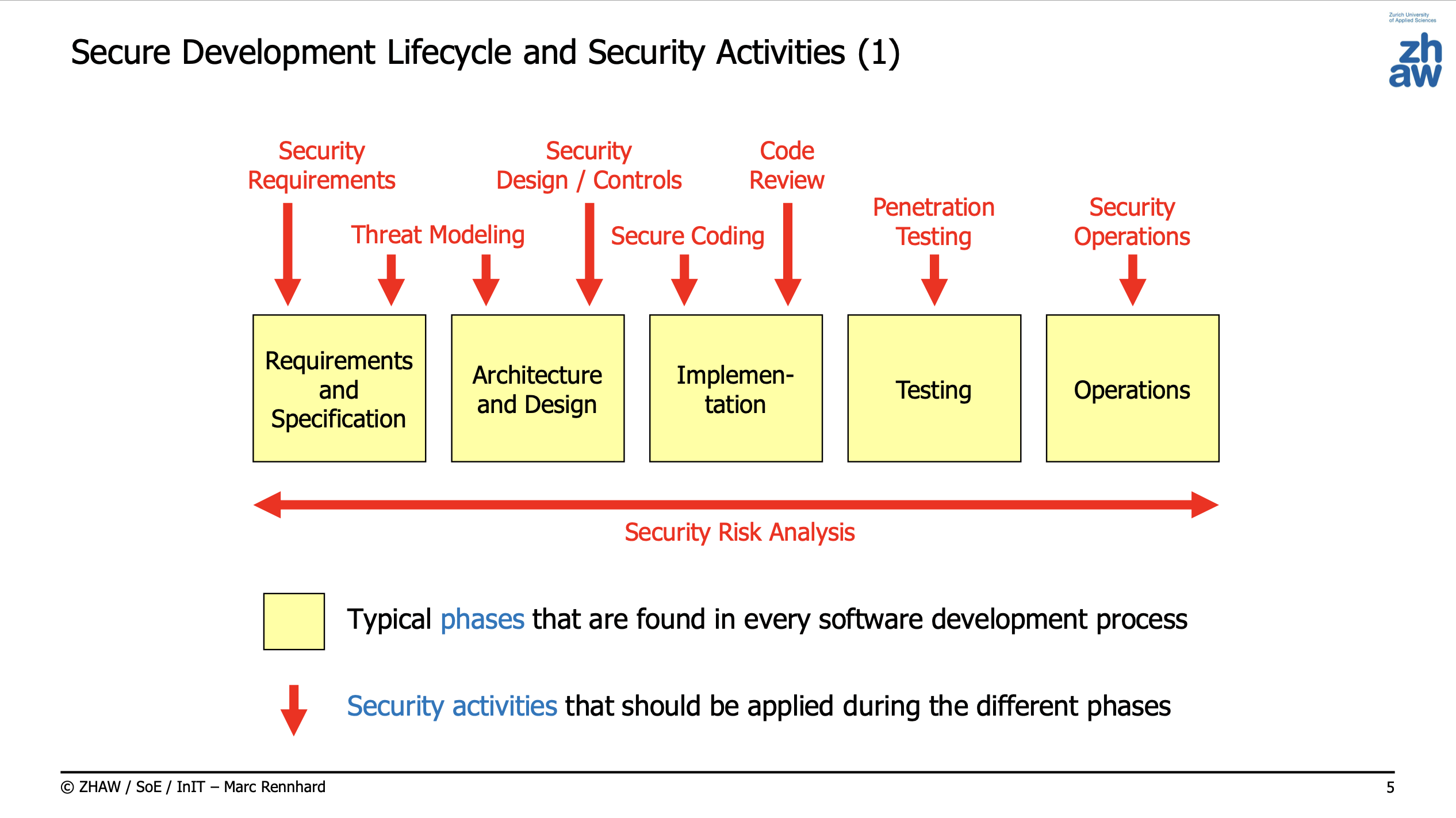
Can be done in a waterfall (every phase is done once) or agile/iterative way (every phase is repeated).
Security Activities
Security Requirements
- Defining security requirements is the first security-related activity that is carried out (based on functional requirements).
- Security requirements should be specific without including implementation details.
Example
If an application transmits credit card information from client to server, this may result in a security requirement that «Communication must be done over a cryptographically protected channel»
Threat Modeling
- Threat modeling is the process of identifying security design flaws in a system based on the security requirements.
Example
- As a possible threat, «getting non-legitimate access to the admin area» is identified.
- If neither the security requirements nor the current security controls clearly show that there must be an access control mechanism where every single access to the web application must be checked, then this is identified as a vulnerability
Security Design / Controls
- Security design is the process of designing security controls that mitigate the identified vulnerabilities and implement the security requirements.
Example
- Security requirement: «Strong user authentication must be used»
- Security design: «Two-factor authentication using a password combined with a biometric fingerprint»
or
- Security requirement: «Prevent buffer overflows»
- Security design: «Use secure allocation functions and enable stack protection, ...»
Secure Coding
- Implementing software according to the security design in a secure way (no
exec(params.permit![:arg])).
Code Review
- Inspecting the code and searching for security problems
Penetration Testing
- Penetration testing means taking the attacker's view with the goal to find and exploit vulnerabilities in the running
system
- To verify whether the security requirements are fulfilled in the implemented system
- To check that no security bugs were introduced during programming
Security Operations
- Security operations are the activities that are carried out after the system is deployed and in operation
- Security operations include:
- Monitoring the system for security-relevant events
- Incident response
- Security audits
- Security maintenance
- Backups
- ...
Security Risk Analysis
- Security risk analysis is a horizontal activity complementary to the other activities
- It is used to rate the risk of problems and to prioritize the security activities